A Simple Guide To Deploying A Site To Site VPN Using Sophos UTMs
by

Etienne Liebetrau
In a previous article we showed how easily you could expand your network out to remote sites using the Sophos RED devices. These little guys are great and they really cater for a wide variety of use cases. They don’t however have the same level of functionality as a full-blown Sophos UTM.
If you have a remote branch site or divisional office that needs more functionality than a RED provides, you can deploy a Sophos UTM to the site and still connect to back to your head office using Site to Site VPN. Reasons for deploying a full UTM compared to a RED include:
- Local Internet breakout with web protection
- Inbound connections
- Locally hosted web applications
- Secondary data center
- Need for fault tolerant ISP
- High Availability cluster
There is a nice spread of Sophos UTM SG devices that cater for all connection sizes, so regardless of how big or small the remote office is, there is a suitable UTM appliance.
The smaller units are rather cost effective. A nice feature of the W range such as the SG115W is that they come with built in Wi-Fi so they can serve as the full connectivity solution for the site.
From a functional level, all models are capable of the same features. The only difference is the throughput you can achieve with them. You can find out more about the different models, along with their specs and capabilities here:
- Tech Specs: https://www.sophos.com/en-us/products/unified-threat-management/tech-specs.aspx#start
- SG Series Appliances Fact Sheet: https://www.sophos.com/en-us/medialibrary/PDFs/factsheets/sophos-sg-series-appliances-brna.pdf?la=en.pdf
Setting Up A Basic Site to Site VPN With Sophos UTMs
There are of course different ways of configuring a two site deployment, depending on the infrastructure, desired protocols, authentication type, crypto strength, etc.
We are going to step through the process of doing a very simply deployment, but it will touch on all the point you will need to learn to configure your own custom Site to Site VPN. This lab contains the following sites and devices:
-
Branch Office
-
Internal Network : 192.168.10.0/24
-
External IP : Dynamic
-
Head Office
-
Internal Network 10.0.0.0/8
-
External IP : Static
In the lab, we will connect the two sites together so that users can transparently share resources with users in the same or remote sites.
We are going to do this using an IPsec VPN tunnel because it is the go-to VPN protocol of choice and offers excellent authentication and encryption strength.
IPsec is also an open standard, so in theory at least, this setup should allow you to connect other non-Sophos-UTM devices in a similar manner.
1. Configuring the Head Office UTM
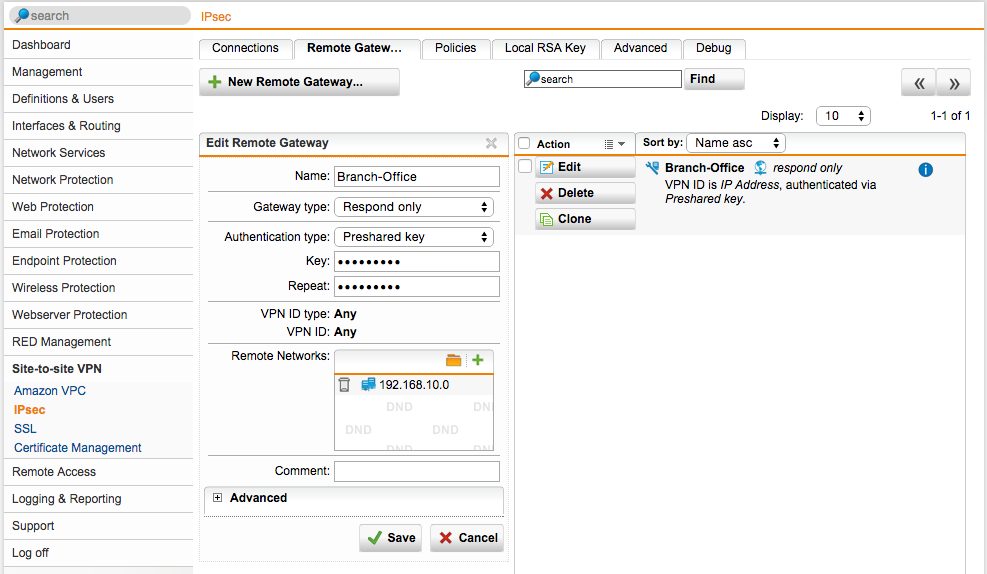
The first thing we need to do is tell the head office UTM about the remote site, it’s network and what to do should it receive a connection attempt from it.
Since the head office has a static IP address, it will be the one that receives the connection attempt and it won’t initiate it.
- Browse to Site-to-site VPN | IPSec | Remote gateway | + New Remote Gateway
- Specify the name of Branch Office
- Gateway type is to Respond Only
- Authentication type is Pre-shared Key. Specify and repeat one.
- Remote network: Define and select 192.168.10.0/24
- Click Save
The second portion of the head office configuration is telling the Sophos UTM how to encrypt the connection to the remote site and what networks to offer it.
- Browse to Site-to-site VPN | IPSec | Connections | + New IPsec Connection
- Specify a name of Branch Office Connection
- Select the Branch office remote gateway created earlier
- Specify the External or WAN Interface
- Select an encryption policy AES-128
- Add the local network you want to share with the remote site (10.0.0.0/8)
- Check the box for Automatic firewall rules
- Click Save
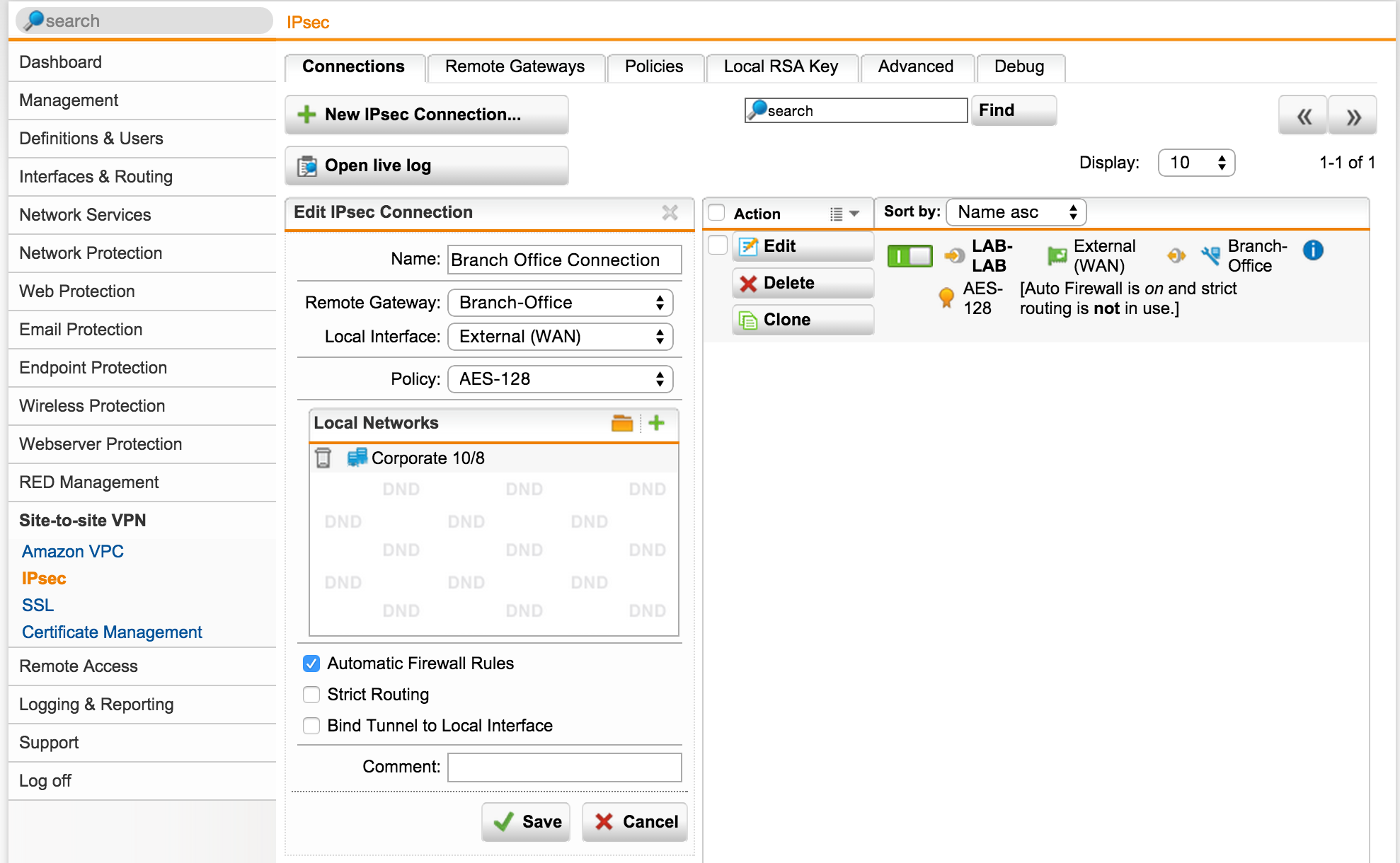
A note on the encryption policy: A number of policies are supported because IPsec is an open standard but not all vendors or device support all the crypto ciphers. The stronger cipher set here is AES-256 PFS that stands for Advanced Encryption Standard 256bits with Perfect Forward Secrecy. It provides excellent security but also comes with a performance hit. Realistically, in most cases AES-128 is going to be just fine, especially for my little lab. You can define your own encryption policy if you really need to, but for UTM to UTM you can safely stick to the default defined policies.
2. Configuring the Branch Office
The branch Sophos UTM will now be configured to initiate a connection with the Head Office UTM. Since it has a dynamic public IP address, the branch office will always be initiating the connection to the head office UTM on its fixed public IP.
First, lets set up the Remote Gateway
- Browse to Site-to-site VPN | IPSec | Remote gateway | + New Remote Gateway
- Specify the name of Head Office
- Gateway type is to Initiate connection
- Gateway Define and add the Head Office public IP
- Authentication type is Pre-shared Key (must match the other side - configured previously)
- VPN ID Type IP Address
- VPN ID (optional)
- Remote network define and select 10.0.0.0/8
- Click Save
Now that the gateway is defined we can go ahead and setup the connection
- Browse to Site-to-site VPN | IPSec | Connections | + New IPsec Connection
- Specify a name of Head Office Connection
- Select the Head Office remote gateway created earlier
- Specify the External or WAN Interface
- Select a encryption policy AES-128 (must match the other side)
- Add the local network you want to share with the remote site (192.168.10.0/24)
- Check the box for Automatic firewall Rules
- Click Save
You can open the Live log and see that the tunnel should be starting to come up and connect. If you want a simple view to see that everything is okay, then just click on Site-to-site VPN on the left hand side and it will show a status view.
3. Testing and Tweaking
Now that the tunnel is up and established you should confirm that everything is working as expected.
Enable traffic logging (Optional)
Because we checked Automatic Firewall Rules, we don’t need to manually go and define them. You should already be able to connect from one site to the other.
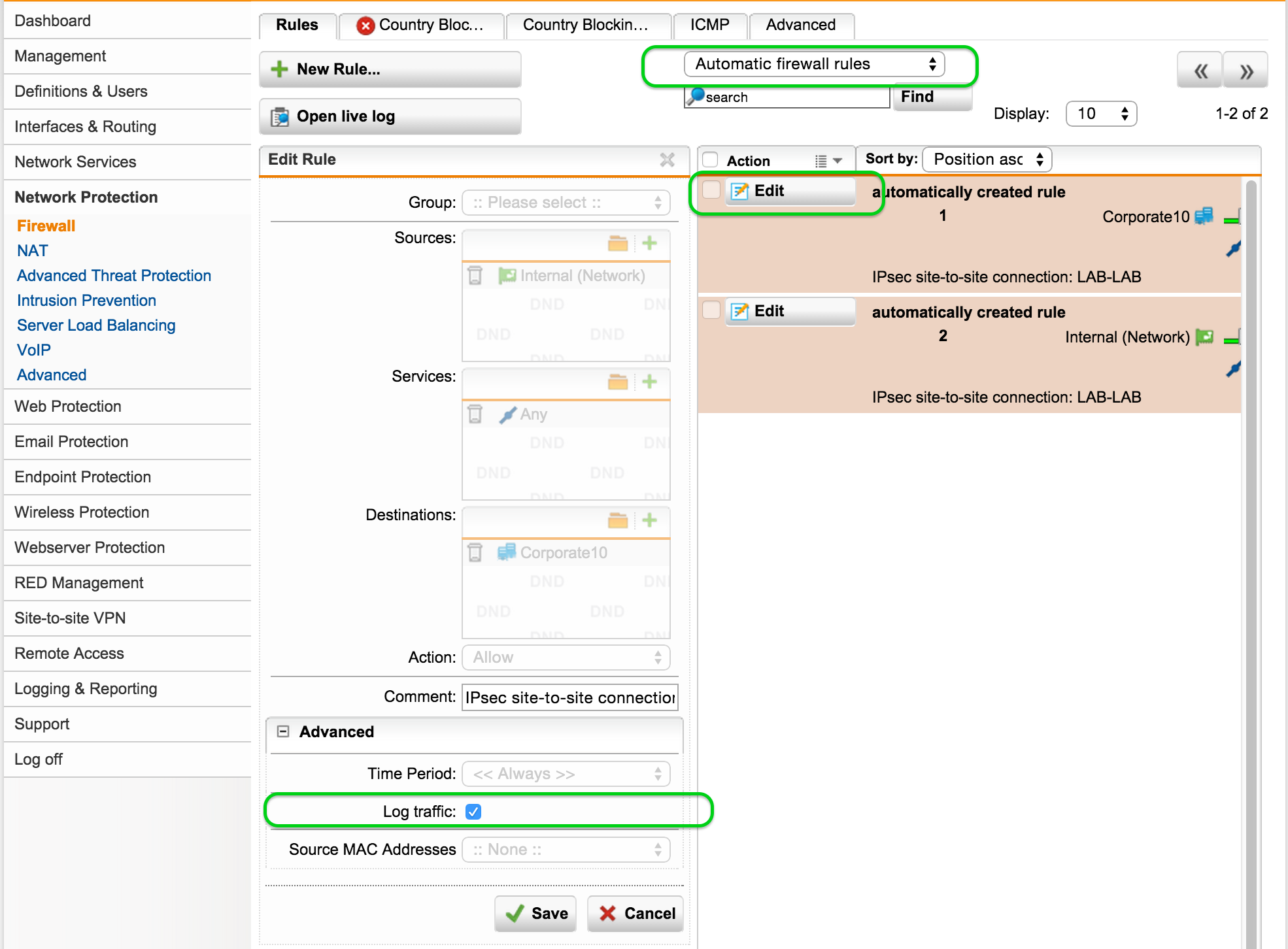
One thing I like to do to ensure everything is working 100% is track the logs. By default the automatically created firewall rules do not log traffic. To fix this do the following.
- Browse to Network Protection | Firewall | Rules | Automatic Firewall rules
- Click the Edit button on a rule
- Check the box for Log traffic
- Click Save
Repeat this for both rules on both sides. That's 4 in total!
Routing Back with Masquerading Rules (Optional Depending)
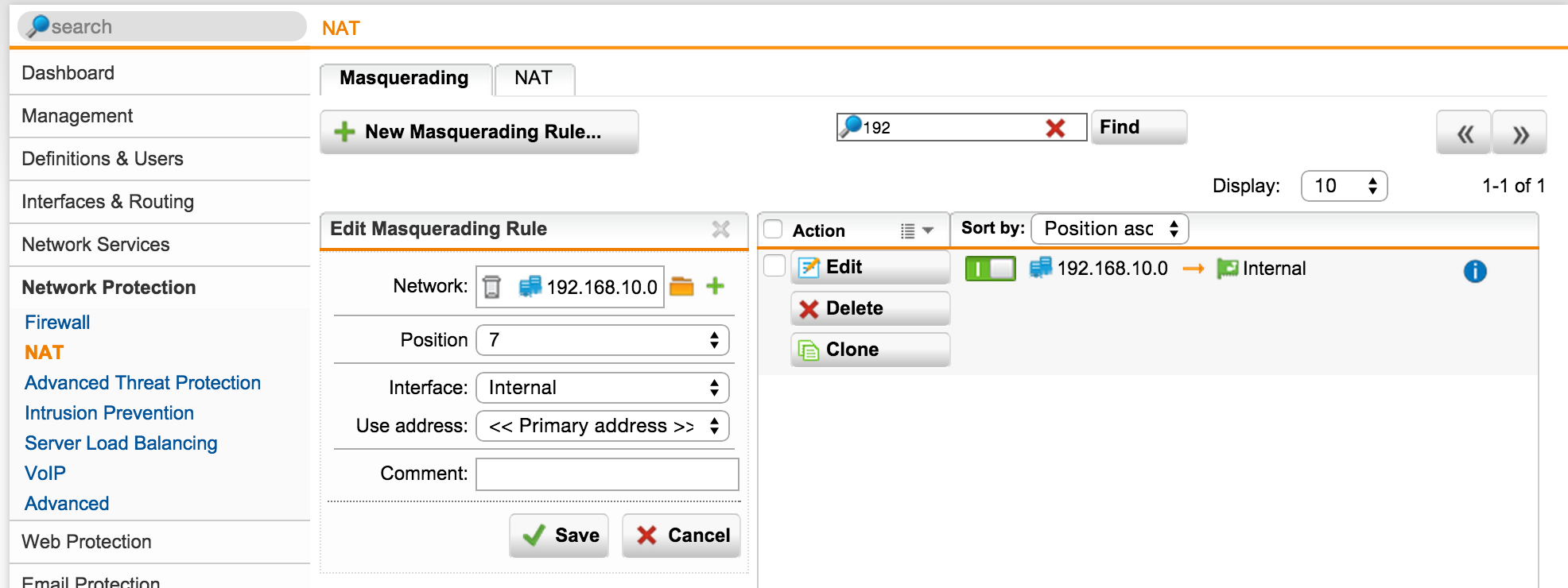
Another step that may be required depending on your environment is to set up Network Masquerading Rules. If the Sophos UTM is your last network default gateway, this step would not be required.
- On the Head Office UTM browse to Network Protection | NAT | +New Masquerading Rule
- Select the remote network we defined in the Branch Office Remote Gateway (192.168.10.0/24)
- For Interface select Internal
- Use Primary Address
- Click Save
Now do the same, but opposite, on the Branch Office UTM
- Browse to Network Protection | NAT | +New Masquerading Rule
- Select the remote network we defined in the Head Office Remote Gateway (10.0.0.0/8)
- For Interface select Internal
- Use Primary Address
- Click Save
You should now be able to send traffic back and forth across the tunnel from either side, requesting or consuming bi-directionally.
4. Reporting on Internet Usage with Fastvue Sophos Reporter
One of the reasons you might want to deploy a Sophos UTM on site compared to a RED, is that you want to allow the users on that site to use the local Internet break out rather than tunnelling back and forth over the RED tunnel. The RED can be set to allow local break out in split tunnel mode but then there is no web protection, filtering or logging. For more information, see our article on the various RED Deployment Modes.
One of the limitations of the Sophos UTM’s “on box” reporting is that it does not scale to multi-site or multi-UTM deployments. If you want to get an aggregated and consistent view of your user's activities regardless of which site they work on, you are going to need some help.
Because the tunnel allows you to use and share resources across the sites, you can configure your Branch office UTM to syslog its web traffic to your head office Sophos Reporter server, and you can have a unified view of the user activity regardless of the site the user is located in.
Even if the tunnel goes down for any reason, you will not lose log data if you have historic log import configured and enabled.
Since Fastvue Sophos Reporter is licensed by user count and not UTM device count there is no penalty or additional cost to adding one or even many additional Sophos UTM devices. You will however just need to request an additional license key when adding each additional UTM.
Conclusion
Sophos UTM allows you to expand your network to remote sites using RED devices, or using Site to Site VPNs using Sophos UTMs or any other IPSec compliant gateway devices.
At all stages of configuring a Site to Site VPN, Sophos UTM provides granular control over tweaking, tuning and restricting access further. This simple lab configuration has hopefully touched on all of the key parts that you need to go out and build your own network of private tunnels across the public network.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Configuring a Site-to-Site VPN Between Sophos UTM (SG) and Sophos XG
How to Configure Multiple Site-to-Site SSL VPNs with Sophos UTM