Configuring a Site-to-Site VPN Between Sophos UTM (SG) and Sophos XG
by

Etienne Liebetrau
In this article, I am going to cover the supported configuration for IPSec site-to-site VPN connections between Sophos UTM (SG) and Sophos XG firewalls.
The main limitation to understand is that site-to-site VPNs are only supported when Sophos UTM (SG) is the initiator, and Sophos XG is the respondent. This may change in the future, but it is certainly the case at the time of writing (January 2018) with SFOS 17.0.3 MR3 and SG 9.506-2.
This is a particular issue if you have NAT on one end but not the other. Typically NAT-T supports the initiator being behind a NAT, but not the respondent. If your central deployment is on Sophos UTM SG (on a fixed public IP), and your branches are on Sophos XGs behind NAT, then Site-to-Site VPNs are not going to work for you.
With that caveat outlined, let's look at how to configure IPSec Site-to-Site VPN connections between your Sophos UTM (SG) and Sophos XG devices.
Part 1. Configure the Sophos UTM (SG)
Let's start by configuring the Sophos UTM (SG) to initiate the connection to the Sophos XG, and allow traffic in and out.
Local and remote network definitions
First, you need to explicitly define the networks that will exist on either end of the VPN tunnel.
- Go to Definitions & Users | Network Definitions | +New Network Definition
- Create a network for the Sophos XG's internal network side.
- Create a HOST for the Sophos XG's public WAN IP.
- Create a Network for the Sophos UTM (SG)'s internal network side.
IPSec Policy
The policy is used to negotiate how the two firewalls secure the connection. Go to Site-to-Site VPN | IPsec |Policies | +New and create a new policy with the following settings:
- Name: UTM_to_XG
- IKE encryption: AES 256
- IKE Authentication: SHA2 256
- IKE SA lifetime: 3600
- IKE DH group: Group2
- IPSEC Encryption: AES 128
- IPSEC auth: MD5
- IPSEC SA lifetime: 3600
- IPSEC PFS: Group2
Configure the Remote gateway
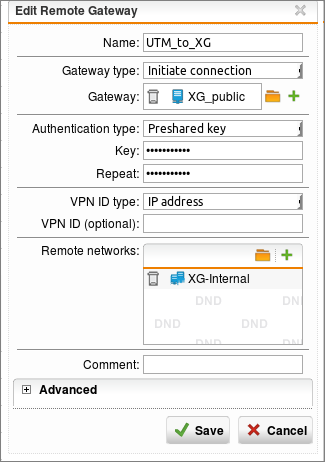
Now we need to define the Sophos XG that our Sophos UTM (SG) will connect to. Go to Site-to-Site VPN | IPsec | Remote Gateways | +New Remote Gateway and create a remote gateway with the following settings:
- Name: XG
- Type: Initiate Connection
- Gateway: The Sophos XG WAN Public host defined earlier (public IP)
- Authentication: Preshared Key
- Key and repeat: Your secure password
- VPN ID Type: IP address
- VPN ID (Optional):
- Remote Networks: The Sophos XG Internal Network object created earlier
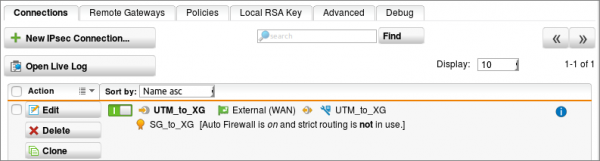
Configure the IPsec connection
This is the portion that will invoke the connection to the XG. Go to Site-to-Site VPN | IPsec | + New IPsec Connection and create a new connection with the following settings:
- Name: UTM_to_XG
- Remote Gateway: The Sophos XG gateway created earlier
- Local Interface: WAN
- Policy: The UTM_to_XG policy created earlier
- Local Networks: The Sophos UTM (SG) Internal network object created earlier (do not just use the green default Internal network object)
Now turn on the IPsec connection by going to Site-to-Site VPN | IPsec and toggle the switch to turn it on.
Configure the Firewall rules
The VPN establishes the connection and adds the routing but it does not define the types of traffic that are allowed or blocked. For that, we are going to define two basic rules; one to allowed inbound traffic and another to allow outbound traffic.
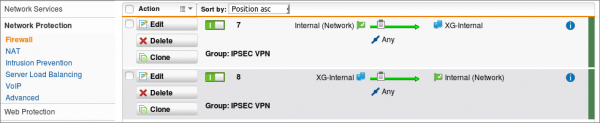
To allow inbound traffic, go to Network Protection | Firewall | + New Rule and add a new rule with the following settings:
- Source: Sophos XG's Internal Network
- Destination: Sophos UTM (SG) Internal Network
- Type: Any
Toggle the switch to turn on the rule.
To allow outbound traffic, go to Network Protection | Firewall | + New Rule and add a new rule with the following settings:
- Source: Sophos UTM (SG) Internal Network
- Destination: Sophos XG Internal Network
- Type: Any
Toggle the switch to turn on the rule.
Part 2. Configure the Sophos XG
Now that the Sophos UTM (SG) has been configured to initiate the site-to-site VPN connection to the Sophos XG, we can configure the Sophos XG to accept and allow the connection as well.
Local and remote network definitions
First, you need to explicitly define the networks that will exist on either end of the VPN tunnel.
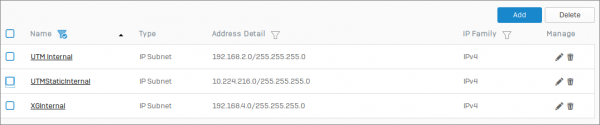
- On the Sophos XG, go to System | Hosts and Services | Add
- Create a network for the Sophos XG's internal network side.
- Create a HOST (IP) for the Sophos UTM (SG)'s public WAN IP.
- Create a Network for the Sophos SG internal network side.
IPSec Policy
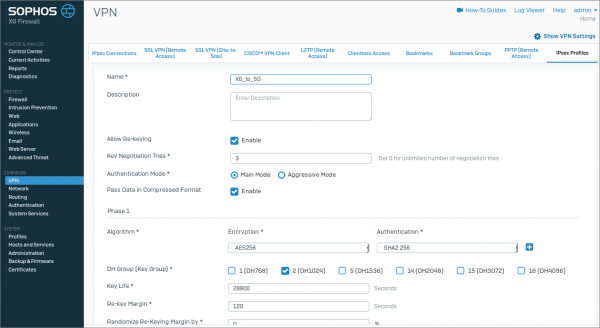
Next, configure a corresponding IPsec policy to match the Sophos SG side. Go to Configure | VPN | … | IPsec Policies, and add a new policy with the following settings:
- Name: UTM_to_XG
- Allow Re-keying: Enabled
- Key Negotiation tries: 3
- Authentication Mode: Main Mode
- Pass Data in Compressed format: Enabled
- Phase 1 Encryption Algorithm: AES 256
- Phase 1 Authentication Algorithm: SHA 256
- DH Group: 2 (DH2014)
- Key Life: 28800
- Re-key Margin: 120
- Dead Peer Detection: Disabled
- Phase 2 Encryption Algorithm: AES 128
- Phase 2 Authentication Algorithm: MD5
- PFS Group: Same as Phase 1
- Key Life: 3600
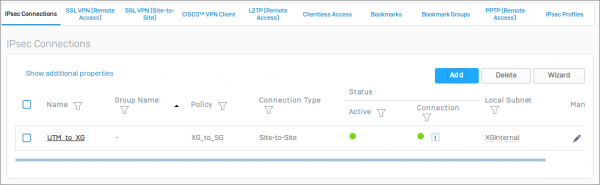
Configure the IPsec gateway and connection
To set up the VPN Connection on Sophos XG, you can use the Wizard. Go to VPN | IPSEC Connections | Wizard and create a connection with the following settings.
- Select Site to site
- Base location: Head Office
- Policy: UTM_to_XG
- Action: Respond only
Authentication Details:
- Type: Preshared Key
- Key: Same as configured on the Sophos UTM (SG)
Local Networks:
- Local Port (Normally Port B)
- IP Family 4
- Local Subnet: Sophos XG Local subnet created earlier
Remote Subnet:
- Remote VPN Server: The WAN IP address of the Sophos SG appliance
- IP Family 4
- Remote Subnet: Sophos SG local subnet created earlier
*Allow NAT Traversal is greyed out – it is automatically adjusted and enabled if required.
Review the settings and Finish:
Enable the IPSec Connection
In the IPSec Connections, click the Active red icon to enable it. It should turn green immediately and the connection indicator should go green within 20-30 seconds.
Configure Firewall Rules
Depending on your deployment you might want granular controls on one side and relaxed firewall rules on the other. I prefer to keep them in sync. Again, let's define two basic rules; one to allowed inbound traffic and another to allow outbound traffic.
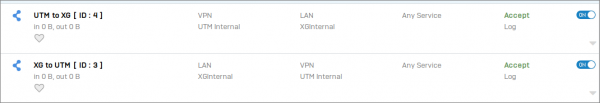
To allow outbound traffic, go to Firewall | +Add firewall Rule and add a new rule with the following settings:
- Name: XG to UTM
- Action: Accept
- Source Zone: LAN
- Source Networks: Sophos XG's LAN
- Destination Zones: VPN
- Destination Networks: Sophos UTM (SG)'s LAN
- Services: ANY
- Match known users: Disabled
- Log Traffic: Enabled
- Save
To allow inbound traffic, go to Firewall | +Add firewall Rule and add a new rule with the following settings:
- Name: UTM to XG
- Source Zone: VPN
- Source Networks: Sophos UTM (SG)'s LAN
- Destination Zones: LAN
- Destination Network: Sophos XG's LAN
- Services: Any
- Match known users: Disabled
- Log Traffic: Enabled
- Save
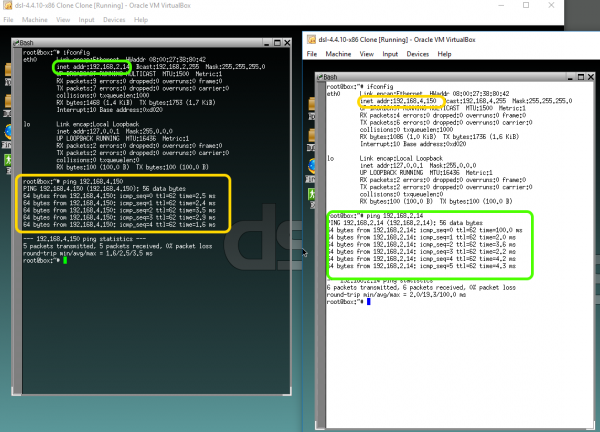
You should see that the site-to-site VPN connection is up on both the Sophos XG and Sophos UTM (SG) sides, and you should be able to send and receive traffic from either side of the tunnel. In this case, I am sending a ping from one network to the other.
IPSec site-to-site VPN connection, success!
Conclusion
Sophos has been making great progress in maturing the Sophos XG platform. It is now a serious contender for deployment instead of the more established Sophos UTM (SG) platform.
There will be a level of crossover as your environment moves from the one platform to the other. But know there is no rush for this process to start. Sophos has stated on numerous occasions that it is dedicated to supporting Sophos UTM (SG) for years to come. However, newer features on the Sophos XG make it more compelling to shift.
Having IPSec site-to-site VPN connectivity between Sophos SG and Sophos XG is a key capability for organizations looking to migrate from the older to the newer Sophos platform. Thus awareness of the current limitations can help you plan for such a project.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
A Simple Guide To Deploying A Site To Site VPN Using Sophos UTMs
Sophos SG and Amazon VPC VPN Setup and Testing Guide