Using Sophos XG's XStream DPI Engine While Enforcing SafeSearch and YouTube Restrictions
by

Etienne Liebetrau
Sophos XG's XStream DPI engine was introduced in version 18, providing better performance over decrypting SSL/HTTPS traffic including TLS 1.3. This effectively replaces the previous 'Web Proxy' decryption engine, however, there are a few features the Web Proxy engine provides that the XStream DPI Engine does not, including SafeSearch Enforcement and YouTube restrictions.
For many organizations (especially education), enforcing SafeSearch and restricting YouTube is a must. Fortunately, with some creative firewall rules, you can get the best of both worlds and enable the faster DPI engine for most traffic while keeping the Web Proxy enabled for the situations that the DPI engine does not cover.
Background
There is an ever-growing need for stronger cryptography on the public web. There have been several enhancements over the years and finally, in August 2018 there was an official consensus to standardize on the new TLS 1.3 protocol (RFC 8446). The iteration from TLS 1.2 took 10 years, longer than any other iteration before, so it is a significant step forward. Together with this, 2020 saw the deprecation of TLS 1.0 and 1.1. Effectively leaving us with (only) TLS 1.2 and 1.3.
What makes TLS 1.3 better?
- Stronger cryptography
- More efficient, faster, and secure key exchange
- Use of insecure legacy crypto suites removed
Greater encryption is usually at odds with network security and performance. In order to protect your network from threats, your firewall needs to be able to 'read' (decrypt) the encrypted traffic. This is done with SSL/HTTPS inspection, which usually comes with a range of issues including bogging down the performance of your firewall.
The Difference Between Sophos XG's XStream DPI Engine vs Web Proxy
Sophos addressed some of these performance issues by releasing their Sophos XG XStream DPI Engine in version 18. Compared to Sophos XG's existing Web Proxy engine, this release introduced a new faster and more capable Deep Packet Inspection (DPI) engine, allowing far greater efficiency and granular control over inspecting HTTPS traffic, including TLS 1.3.
The new XStream DPI engine approach introduces a few changes to the way the traffic is handled and correspondingly, there are some design choices you need to make.
Here is a breakdown of the main differences between Sophos XG's two methods of inspecting SSL/HTTP traffic:
| Web Proxy | XStream DPI Engine |
|---|---|
| Need to configure client operating systems, browsers, and applications to use the proxy. * | The XG acts as an inline transparent firewall/proxy. No client configuration is needed. |
| Need to deploy the firewall’s certificate to all endpoints using the proxy for SSL decryption to work. | Need to deploy the firewall’s certificate to all endpoints for SSL decryption to work. Multiple Certificate CA’s possible |
| Only decrypts up to TLS 1.2. | Decrypts TLS 1.3 |
| Web proxy transparently handles traffic only on TCP ports 80 and 443. | DPI engine detects and filters HTTP and SSL/TLS traffic on any port. |
| Web proxy optionally decrypts traffic on TCP ports 80 and 443. | DPI engine applies granular SSL/TLS inspection rules for policy-driven decryption. |
| Not as performant as the new DPI engine. | More performant than the Web Proxy |
| Supports SafeSearch, YouTube restrictions, login domains for Google apps, caching and pharming protection. | Does NOT support SafeSearch, YouTube restrictions, login domains for Google apps, caching and pharming protection. |
* It is technically possible to use the Web proxy engine in a transparent proxy mode but given the HTTP/HTTPS port 80 and 443 restrictions you would inevitably also need to deploy some DPI based rules.
Using XStream DPI Engine While Keeping Web Proxy Features
If your environment only uses in-line/transparent proxy and you have no need for SafeSearch or YouTube restrictions then your clear choice is to go with a 'DPI only' model.
However, it is not an all-or-nothing approach. If you need to ensure that SafeSearch is enforced but still want to make use of the XStream DPI engine where you can, then you can deploy a combination of Web Proxy and DPI rules to get the best of both methods.
Let's give it a go!
Configure a Rule for Sophos XG's XStream DPI Engine
First of all, let's create some rules to inspect the bulk of your traffic with the new XStream DPI engine.
- Select Protect | Rules and policies | Firewall rules.
- Edit an existing rule or add a new firewall rule called "DPI Traffic" (for example).
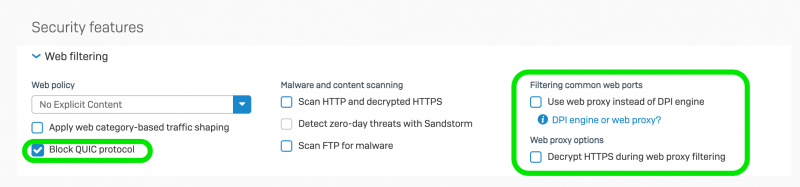
- Under Security features | Web filtering make sure that you
- Select a valid Web policy. E.g. No Explicit Content.
- Check Block QUIC protocol (if you're wondering why, see our article on How Google’s QUIC Protocol Impacts Network Security and Reporting)
- Uncheck Use web proxy instead of DPI engine
- Uncheck Decrypts HTTPS during web proxy filtering
This configuration allows you to utilize the new DPI engine leveraging the strongest available cryptographic security.
Configure an SSL/TLS Inspection Rule to Block Insecure SSL
To tell the DPI engine to inspect TLS traffic you have to set the SSL/TLS inspection rules.
- Select Protect | Rules and policies | SSL/TLS inspection rules.
- Add a rule to Decrypt and inspect by specifying the following:
- Rule name: DPI Inspect Everything
- Action: Decrypt
- Check Log Connections
- Decryption profile: Block insecure SSL
- Add a rule to exclude inspecting certain sites (Optional), by specifying the following:
- Rule name: Exclude Web Categories
- Action: Don't decrypt
- Check Log Connections
- Decryption profile: Block insecure SSL
- Under Website | Categories and websites, add the categories you don't want to inspect (e.g. Financial Services, Health & Medicines)
- Place this rule above of the 'DPI Inspect Everything' rule
- Turn on the toggle switch for SSL/TLS inspection if you haven't already.
Configure a Rule for Sophos XG's Web Proxy Features
Now that Sophos XG is configured to decrypt the bulk of traffic using the XStream DPI engine, let's configure a rule that uses the Web proxy method in order to enable SafeSearch:
- Select Protect | Rules and policies | Firewall Rules.
- Edit an existing rule or add a new firewall rule and specify the following
- Name: WebProxy rule
- Action: Accept
- Check Log Firewall traffic
- Under Destination and Services | Destination networks, Search for "google" and add all the items. Likewise, if you want to enable YouTube restrictions, search for 'youtube' and add all the items.
- Under Security features | Web Filtering make sure that you:
- Select a valid Web policy. E.g. No Explicit Content. Make sure the policy has Search engine enforcement setting turned on in Protect | Web)
- Check Block QUIC protocol (Again, if you're wondering why, see our article on How Google’s QUIC Protocol Impacts Network Security and Reporting)
- Check Use web proxy instead of DPI engine
- Check Decrypt HTTPS during web proxy filtering
- Place this rule above the DPI traffic rule
Don't Forget to Distribute the SSL Certificate!
When deploying any sort of SSL/HTTPS Inspection, your client devices will all need to trust your Sophos XG as a Certificate Authority to issue certificates for all of the web traffic. The certificate you need to install on the client devices/browsers is under System | Certificates | Certificate authorities | SecurityAppliance_SSL_CA. Additional guidance on this is available here: Sophos XG Firewall: SSL CA certificate installation guide.
Testing Tip: Apply the policies to your own IP first, then roll it out to everyone once you've confirmed it is working.
Testing Sophos XG's SSL Decryption
There are three scenarios we want to confirm:
- SafeSearch is being enforced
- Banking websites are not being inspected (optional)
- DPI is used for most traffic, including TLS 1.3.
An easy way to confirm we're getting the behavior we want is to use Google Chrome's DevTools (Command+Option+I (Mac) or Control+Shift+I (Windows)), and browsing to HTTPS websites.
Testing SafeSearch is Enforced
To test SafeSearch, browse to www.google.com and perform a search with the Google Chrome DevTools open. The screenshot below shows SafeSearch is being enforced, the TLS Level is 1.2 (as expected through Web proxy mode) and the certificate is signed by the Sophos SSL CA.
Testing the XStream DPI Engine is Active
To test TLS 1.3 is being decrypted, browse to https://kinsta.com (a site that currently supports TLS 1.3). You can see that the traffic is inspected, the signing CA is again the Sophos SSL CA, but this time the TLS version is 1.3. Something to keep in mind during testing is that unless the originating site supports TLS 1.3 (like https://kinsta.com/ does) you will only see TLS 1.2 (like https://cnn.com at the time of writing).
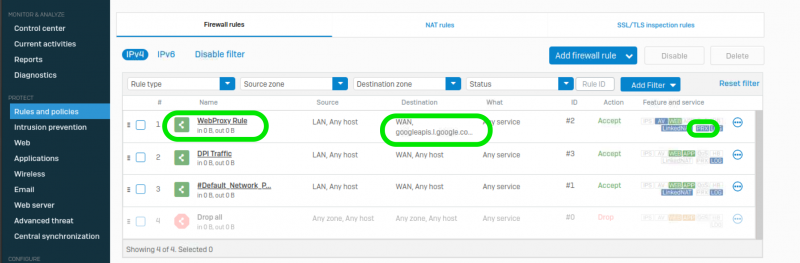
Reporting on Firewall Rules
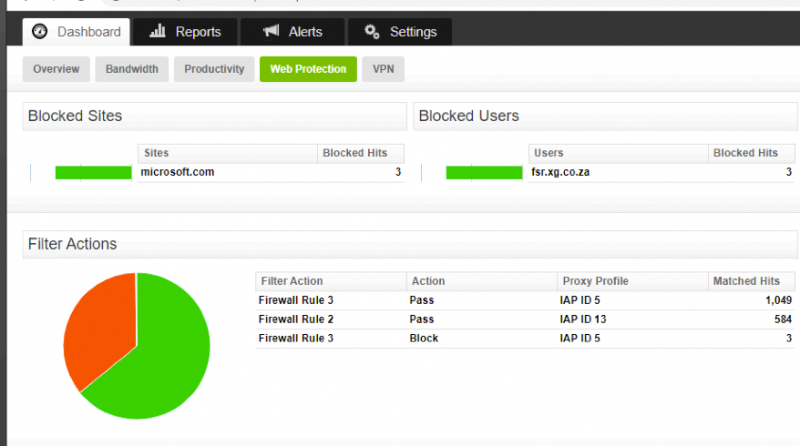
Fastvue Sophos Reporter makes verifying the traffic going through each of your firewall rules really simple. Go to Dashboard | Web Protection and take a look at the Filter Actions section to get an idea of how much data is being allowed or blocked through each of your rules.
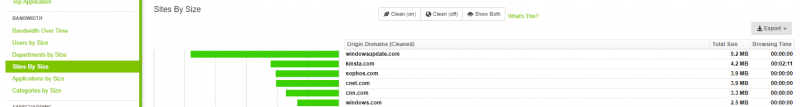
Hover over your DPI Rule (note the firewall rule ID in Sophos XG's UI) and click the green arrow to run a report on the rule. From here we see the sites tied to the rules. From this, I can see that the same rule was used for both kinsta.com and cnn.com.
To get started with Fastvue Sophos Reporter, download the free 30-day trial.
Conclusion
TLS 1.3 is faster and more secure than the previous cryptographic protocols, but decrypting TLS 1.3 is only available with Sophos XG's new XStream DPI engine. Unfortunately, some features are not supported with the XStream DPI engine such as SafeSearch enforcement and YouTube restrictions. Thankfully we can use a rule combination such as the one described above to give us a "best of both" mix of security, performance, and filtering.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)
Sophos XG - How to Block Searches and URLs with Specific Keywords