Mitigate DNS Exploits with Forefront TMG
by

Etienne Liebetrau
What’s in a name? Generally speaking TCP/IP relies on DNS to function. Without DNS all connections would have to be specified by IP address directly. But even specifying an IP address is not enough, as most web hosting environments serve multiple websites from a single IP and use the HOST header to differentiate sites. Effectively without DNS there is no Internet like we know it.
I started off by saying generally speaking. That is because DNS is not the only name resolution mechanism that can be used. For a Windows machine there is a clearly defined order and preference.
How it Works
When a domain name is queried with a PING request the following sequence is followed:
- The client checks to see if the name queried is its own
- The client then searches a local Hosts file
- Domain Name System (DNS) servers are queried.
- If the name is still not resolved, NetBIOS name resolution sequence is used as a backup. This order can be changed by configuring the NetBIOS node type of the client.
(https://support.microsoft.com/kb/172218)
DNS Exploits
Name resolution issues can cause headaches when trying to get things to work, but a far more serious problem from a security perspective is DNS cache poisoning. The basic concept is to change the destination IP address of a valid name. Traffic will then be routed to the malicious site instead of the intended site.
As an example, if the DNS records for Facebook are compromised, login credentials could easily be harvested by redirecting users to a “fake” Facebook site that look real enough for users to enter their credentials. This concept if often referred to a pharming.
The importance of DNS was illustrated recently when GoDaddy's DNS servers were down and all hosted sites became unavailable.
The name resolution attack vector can be approached in a number of ways. Here are some examples:
Compromise HOSTS File
The easiest and most effective target is to compromise the local HOSTS file. The reason for this is because this is a simple text file on a computer. It can be edited without any complex methods. It is also first in line for name resolution so a compromise here is extremely effective.
Compromise DNS Servers
The second is to compromise DNS servers directly. This is a far more complex undertaking and as such is seen far less frequently.
Compromise Network Equipment
A third method is a combination approach of the first two, as it involves attacking network equipment such as consumer DSL routers and directing DNS requests to a server controlled by a malicious party.
DNSchanger was a widely publicized piece of Malware that also exploited naming vulnerabilities.
DNS Exploits in Practice
The steps below will illustrate the problem presented by a compromised a HOSTS file. For this example I am using yahoo.com.
Compromise the HOSTS file
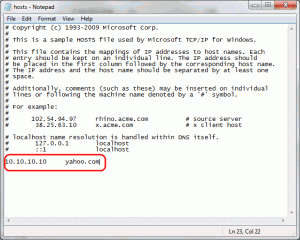
- Copy the HOSTS file from "c:\Windows\System32\drivers\etc\" to the desktop
- Edit the file in notepad and add the following line 10.10.10.10 yahoo.com
- Save the file and copy it back to "c:\Windows\System32\drivers\etc\" (You will probably get a Windows UAC challenge here).
Verify the compromise
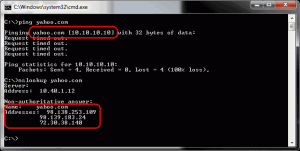
- Open a command window.
- PING yahoo.com
- Notice it returns the IP 10.10.10.10
- Now force a DNS lookup with.
- NSLOOKUP yahoo.com.
- Notice the actual values are returned.
Test the hack
- Launch Internet Explorer.
- Browse to any site (other than yahoo) and see that everything is working as expected.
- Now attempt to browse to yahoo.com.
- If you are using a direct internet connection your connection will not go anywhere.
Exploit the hack
- On a non-compromised machine - Open the original site (yahoo.com)
- Save the page as Webpage,complete
- Edit some of the HTML content and links using a text editor.
- Set up an empty IIS web site on 10.10.10.10
- Post your fake site as the default landing page.
- On the compromised machine browse to yahoo.com.
The image shows both the original and hacked site. This was a very quick and basic hack but you can see how effective this can be to catch out the average user.
The reason this happens is that Internet Explorer, like PING, will resolve the name in the usual manner. Picking up our compromised yahoo.com record from the HOSTS file and using that IP.
Mitigate DNS Exploits with Forefront TMG
If however you are using Forefront TMG as a proxy, you will still correctly be routed to the site.
The reason Forefront TMG prevents this exploit is because the client’s HTTP request is sent to the Forefront TMG proxy server. The TMG proxy does the DNS lookup on the client’s behalf, determines the correct IP and directs the traffic there.
Forefront TMG itself follows the same name resolution sequence as the client. The name lookup sequence when using TMG as a proxy is as follows:
- Client browser performs a HTTP request for a specific site.
- The request is evaluated against proxy exclusions (auto-configuration script or manual).
- The web request is sent to the Forefront TMG proxy.
- Forefront TMG checks the local HOSTS file entries.
- DNS servers are queried by TMG server.
So if the HOSTS file on TMG has been compromised or purposefully edited, those addresses would be used instead of being resolved via DNS. You could therefore potentially use the HOSTS file as a very crude URL Filtering mechanism.
It is important to note that this behaviour is only for proxy clients. If you are using TMG as a secure NAT client this does not apply.
Conclusion
As you can see Forefront TMG can mitigate name resolution related attacks for your corporate users, providing Forefront TMG's own naming configuration is sound.
Returning to the opening question. What’s in a name? As it turns out, it is quite a bit!
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Make The World A Better Place with Fastvue and Microsoft Reputation Services (MRS)
How to Report on YouTube Activity with Fastvue TMG Reporter