Deploying Endpoint Protection Web Control with Sophos UTM
by

Etienne Liebetrau
Sophos UTM is an excellent secure web gateway capable of filtering and cleaning web traffic, but it also has a special trick when it comes to protecting endpoint computers both on and off premises.
Sophos started out as an anti-virus company, providing endpoint protection for Windows systems. Sophos Endpoint Protect (SEP) is still a core strength in their business, but they have traditionally focused on Enterprise clients, and not the consumer market. Given the complexity and infrastructure requirements of setting up a Sophos Enterprise Console (SEC) to manage endpoints, a lot of smaller companies opted for cloud managed or un-managed deployments.
However, Sophos UTM actually gives you the ability to protect and manage your Windows endpoints with the Sophos Endpoint Protect product, without the need to set up any additional management infrastructure. You can do it all directly from the UTM. If you do have a Sophos Enterprise Console, check out our companion article on SEC and Sophos UTM integration.
Getting Started with Sophos UTM Endpoint Protection
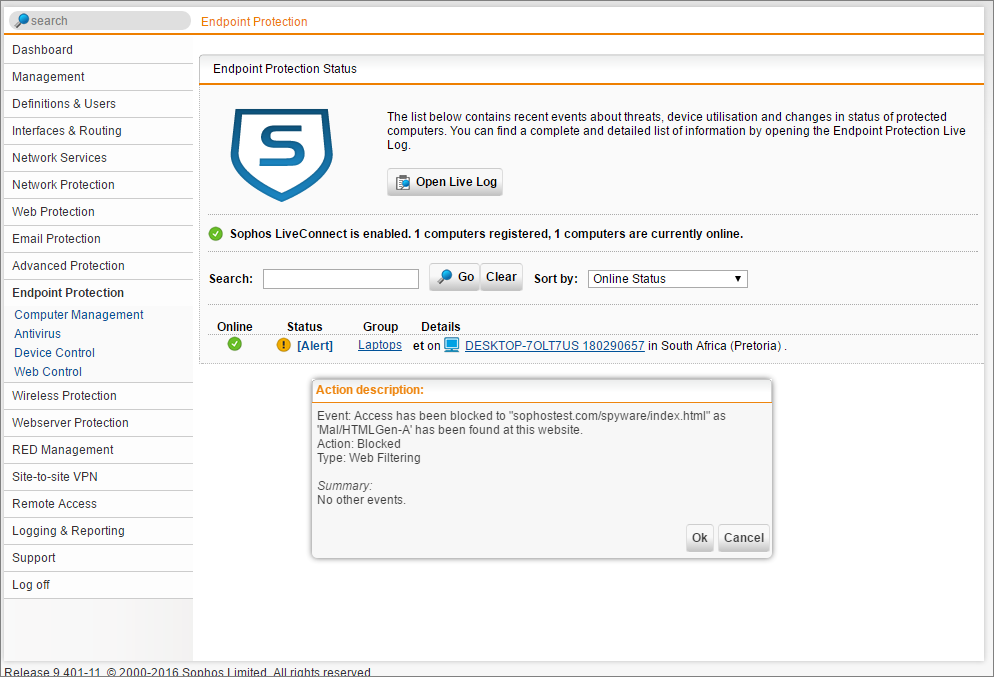
To enable Sophos UTM Endpoint Protection, browse to Endpoint Protection | Computer Management | Global and toggle the switch for Endpoint protection status.
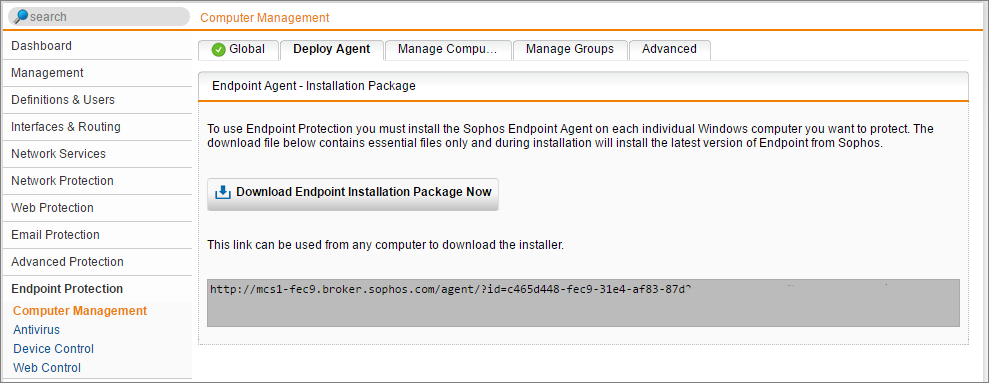
Next, you need to install the Endpoint Protection agent on your devices. To do this, go to Endpoint Protection | Computer Management | Deploy Agent. You can link to the agent directly from the management console, or you can copy and distribute the link.
Once the agent is installed, allow a couple of minutes for the device(s) to show up as a managed computer. Once the devices have registered themselves with the UTM, they can be selected and placed into groups. The groups are used to manage the different endpoint protection policies that we apply to the devices.
Defining Sophos UTM Endpoint Protection Policies
There are three policy types you can create:
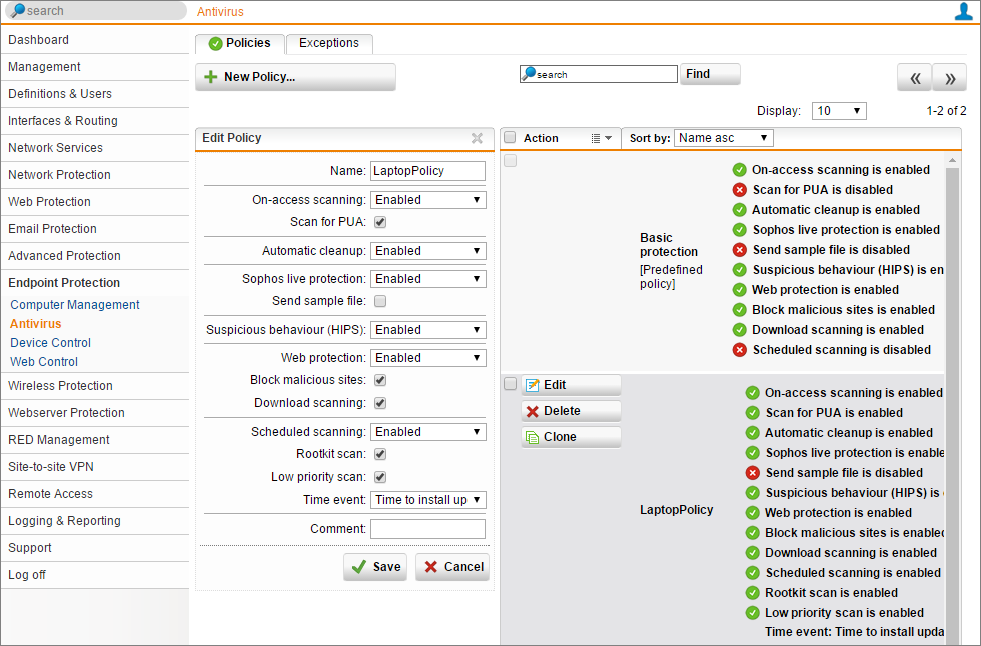
Antivirus Policies
This allows you to specify the policy settings for the traditional Antivirus or anti-malware control. This is from the Sophos documentation explaining the settings:
On-access scanning: If enabled, whenever you copy, move, or open a file, the file will be scanned and access will only be granted if it does not pose a threat to your computer or has been authorized for use.
Scan for PUA: If enabled, the on-access scanning will include a check for potentially unwanted applications (PUAs).
Automatic cleanup: If enabled, items that contain viruses or spyware will automatically be cleaned up, any items that are purely malware will be deleted, and any items that have been infected will be disinfected. These disinfected files should be considered permanently damaged, as the virus scanner cannot know what the file contained before it was damaged.
Sophos live protection: If the antivirus scan on an endpoint computer has identified a file as suspicious, but cannot further identify it as either clean or malicious based on the Sophos threat identity (IDE) files stored on the computer, certain file data (such as its checksum and other attributes) is sent to Sophos to assist with further analysis.
Send sample file: If a file is considered suspicious, but cannot be positively identified as malicious based on the file data alone, you can allow Sophos to request a sample of the file. If this option is enabled, and Sophos does not already hold a sample of the file, the file will be submitted automatically.
Suspicious behavior (HIPSClosed): If enabled, all system processes are watched for signs of active malware, such as suspicious writes to the registry, file copy actions, or buffer overflow techniques. Suspicious processes will be blocked.
Web protection: If enabled, the website URLs are looked up in the Sophos online database of infected websites. (*Note here* this is not the same as Web Control - this is very basic malicious site blocking only)
- Block malicious sites: If enabled, sites with malicious contents will be blocked.
- Download scanning: If enabled, during a download data will be scanned by antivirus scanning and blocked if the download contains malicious content.
Scheduled scanning: If enabled, a scan will be executed at a specified time.
- Rootkit scan: If enabled, with each scheduled scan the computer will be scanned for rootkits.
- Low priority scan: If enabled, the on-demand scans will be conducted with a lower priority. Note that this only works from Windows Vista Service Pack 2 onwards.
- Time event: Select a time event when the scans will take place, taking the time zone of the endpoint into account.
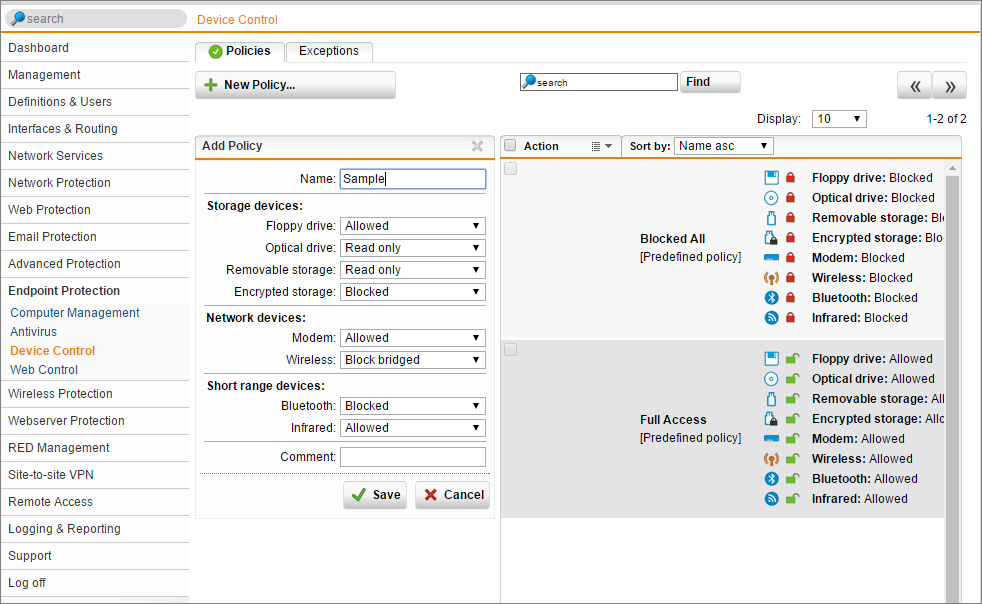
Device Control Policies
Storage Devices allow you to grant permission to Read, Write or Block Access to different device types. The supported devices are:
- Floppy Drive
- Optical Drive
- Removable Storage
- Encrypted Storage
Network Devices allows you to Allow, Block or Block Bridged. The supported networks are:
- Modem
- Wireless
Short Range Devices allows you to Allow or Block access. The devices covered here are:
- Bluetooth
- Infrared
Web Control Policies
The Web Control feature enables you to extend similar web protection to users when they are roaming, not just when they are on premises. The differences between Endpoint Web Control and the full Web Protection feature are explained further below.
The policies and settings for Web Control are actually configured under Web Protection using a new profile:
- Go to Web Protection | Web Filter Profiles | + New Profile
- On the Web Filter Profile tab, give the profile a name and add your endpoint group to the Allowed endpoint groups list
- Ignore the HTTPS tab, as HTTPS settings do not apply to endpoint devices.
- On the Policies tab, specify a filter policy without specifying users. Only policies applied to 'all users' will be applied to the endpoint group.
- Save the new Profile.
Applying Endpoint Protection Policies to Devices
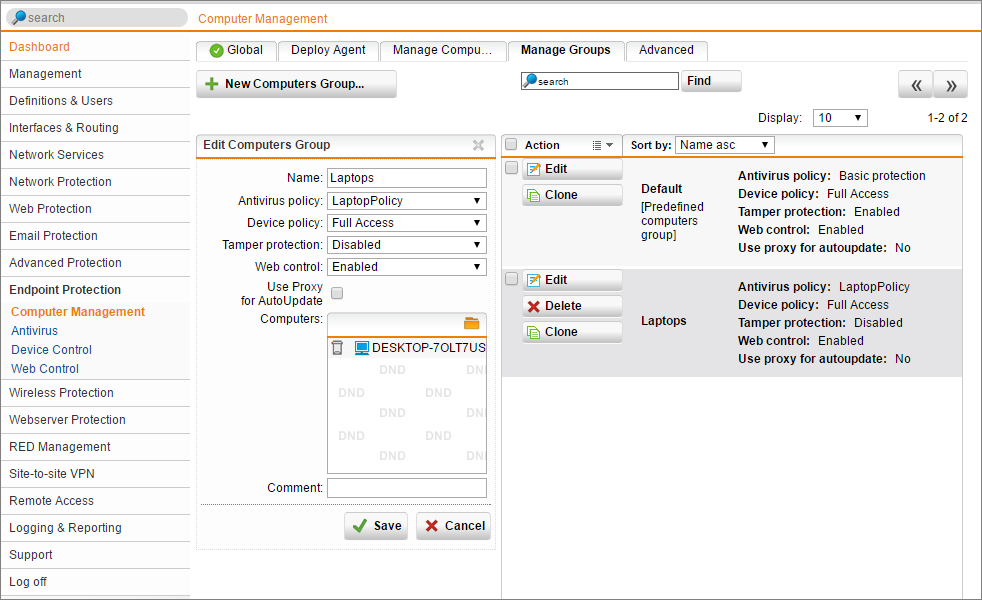
Now that a set of policies are defined, create a device group and add your device(s) to it. Then select the policies to apply to that group.
- Navigate to Endpoint Protection | Computer Management | Manage Groups | New Computers Group
- Specify a name
- Select an Antivirus policy created earlier
- Select a Device Control Policy
- Turn Tamper Protection on or off.
- Enable Web Control
- Add your device(s)
*Tamper protection: If enabled, modification of the protection settings on the respective endpoints locally is only possible with a password. The password is defined on the Advanced tab.
Logging and Reporting of Endpoint Web Browsing Activity
Having the ability to protect users is great, but having the ability to see that the filtering is being applied correctly and that users behave with corporate equipment both in and out of the office is even better!
When connected to the Internet, the endpoint will always connect back to Sophos UTM for status updates and for logging the web traffic activity.
The log data is stored in the Endpoint Web Protection Log on the UTM. If this is log type is checked in the syslog options, Fastvue Sophos Reporter will analyze this data in addition to the normal Web Protection data, to provide a complete browsing history for users both in and out of the office.
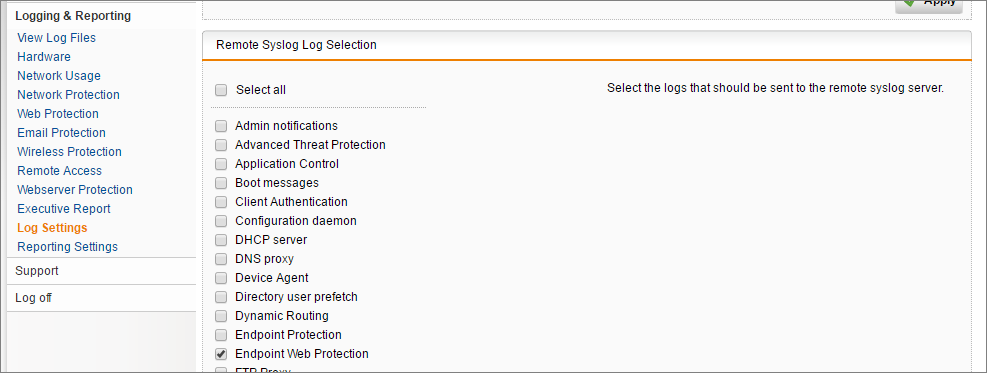
- To add the log source navigate to Logging & Reporting | Log Settings | Remote Syslog Server
- Here you would typically already have the Fastvue Sophos Reporter specified as a destination and the Web Protection logs would be checked. Check the box for Endpoint Web Protection and click Apply.
Note that the web log data for the roaming users gets batched and sent through on a frequent interval. It is not live streaming in the same way it does on-premises.
This may affect the live view in Fastvue Sophos Reporter, but once the data arrives, it will trigger alerts, be inserted into the live dashboards and included in reports as normal.
Unfortunately, the Endpoint Protection log is not as comprehensive as the regular Web Protection log. One of the missing fields is Referrer, which plays a large role in Fastvue's Site Clean feature. At this point in time (UTM firmware 9.403-4), the Site Clean feature will be less effective for Endpoint Protection logs until Sophos update the logging.
Differences Between Endpoint Web Control and Web Protection
As mentioned, there are some differences between the Web Control feature that runs on the endpoint, compared to the full Web Protection feature that runs on the UTM.
The following features are not supported in Endpoint Web Control
- Scan HTTPS (SSL) Traffic
- Authentication Mode
- Antivirus/Malware (Sophos Endpoint will always scan, but Dual scan and Max scanning size are not available)
- Active Content Removal
- YouTube for Schools
- Certificate checks
- Streaming settings
- Block un-scannable and encrypted files
- Block by download size
- Allowed target services
- Web Caching
It may seem that you are losing a lot, but keep in mind that Sophos UTM Endpoint Protection will handle most of these features for you. Sophos UTM would normally shield the endpoint from this, but as you can imagine, Sophos Endpoint is quite capable on its own.
One important note is that endpoint devices with a policy will receive the same web filtering, regardless of the user that is logged onto it. For this reason you should always set the Sophos Live Protect policy below user specified policies on the UTM.
Conclusion
Sophos UTM's Endpoint Protection management is great for small to medium size deployments. It does not scale to the same level that the Sophos Enterprise Console does, but it provides a great way to protect and monitor both the perimeter and internal network as well as roaming users.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
Deploying Endpoint Protection with Sophos UTM and Enterprise Console
How to Configure Multiple Site-to-Site SSL VPNs with Sophos UTM