Improving the Performance of Sophos XG's Intrusion Prevention System (IPS)
by

Etienne Liebetrau
Sophos Intrusion Prevention System (IPS) is an advanced firewall feature that protects your network. The downside is that IPS is a resource-intensive process, as it needs to match every packet with thousands of attack signatures. This article will show you how to through fine-tune your Sophos XG rules and IPS policies and deploy Sophos IPS with minimal impact on the device's performance.
About Sophos Intrusion Prevention System
A general definition of an IPS is:
An Intrusion Prevention System (IPS) is a network security/threat prevention technology that examines network traffic flows to detect and prevent vulnerability exploits.
As an inline security component, the IPS must work efficiently to avoid degrading network performance. It must also work fast because exploits can happen in near real-time. The IPS must also detect and respond accurately, so as to eliminate threats and false positives.
Sophos uses Snort for its IPS functionality. Don’t be fooled by the Pig Logo or the GPLv2 open source license. Snort is a Cisco company, which gives it some serious commercial enterprise backing. Sourcefire, the creators of Snort, was acquired by Cisco back in 2013.
The Snort IPS engine is one of the most sophisticated IPS systems available. In fact, it is the most widely deployed IPS worldwide. Just turning on the default IPS LAN to WAN profile for your internet break out will put it in a great position as far as protection is concerned.
Enabling the Sophos Intrusion Prevention System
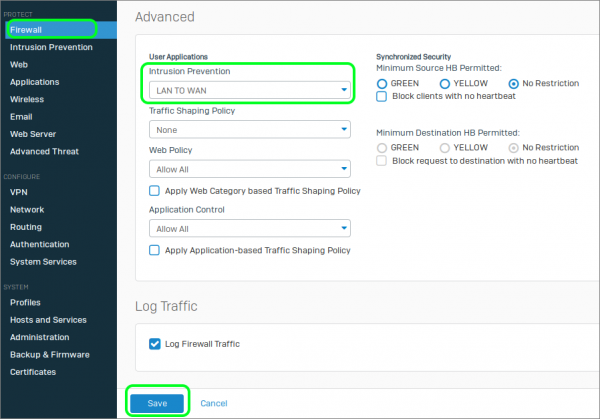
To enforce IPS on a particular firewall rule, follow these steps:
- In Sophos XG, navigate to Protect | Firewall
- Edit the #Default_Network_Policy (or relevant rule name)
- In the Advanced section under Intrusion Prevention select LAN TO WAN
- Click Save
Sophos XG IPS Updates
Updating of rules and signatures is done continuously as part of the Sophos Intrusion Prevention System definition updates. These apply to the default rules, so in theory, IPS dynamically gets updated by Snort and Sophos to always apply for the best protection from emerging threats. As such IPS, despite the advanced protection it offers, is relatively easy to implement and low in maintenance overhead.
Improving Sophos IPS Performance
In an environment where you have low bandwidth utilization and loads of spare resources, you could leave it like this and accept the additional scanning overhead for the benefit of overall security.
But with Sophos XG, you can go a little further and ensure the relevant IPS policies are in place on the appropriate firewall rules, making the overall feature much more efficient, and improving the performance of Sophos XG.
Sophos IPS Policies
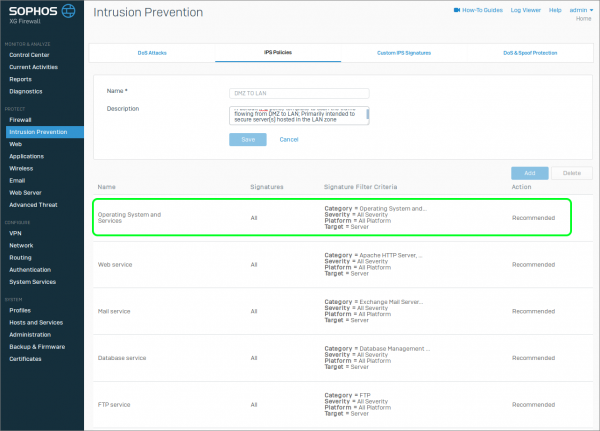
Let's get into how the IPS policies are configured. If we look at one of the default IPS policies, we can see the break down as follows:
- Name: This is the category of the IPS signatures.
- Signatures: This covers which IPS signatures belong in each category.
- Signature Filter Criteria: This further filters the IPS signatures that will be used.
- Action: This defines the response the IPS will have to a triggered event. Depending on the definition, the action can be either warn or block.
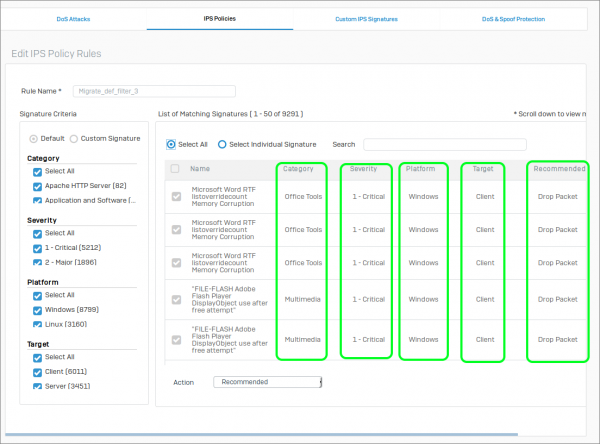
If we dive a litter deeper into what actually makes up the Policy Rules we see the signature details:
You can see that IPS signatures are matched against multiple criteria:
Category Apache HTTP Server (82) Application and Software (1417) Browsers (652) Database Management System (176) DNS (51) ERP System (58) Exchange Mail Server (3) FTP (53) Industrial Control System (272) Malware Communication (2609) Microsoft IIS web server (4) Misc (416) Multimedia (774) Office Tools (630) Operating System and Services (1070) Other Mail Server (63) Other Web Server (18) Reconnaissance (94) Sendmail (1) VoIP and Instant Messaging (69) Web Services and Applications (779)
Severity 1 - Critical (5212) 2 - Major (1896) 3 - Moderate (1962) 4 - Minor (177) 5 - Warning (44)
Platform Windows (8799) Linux (3160) Unix (1560) Mac (2557) Solaris (1544) BSD (1271) Other (1354)
Target Client (6011) Server (3451)
Based on these, you can see that it is possible to selectively exclude or include IPS scanning for Platforms that may not exist in your environment.
For example, by not scanning for Unix, Solaris and "Other Operating systems" you reduce the IPS signatures being used by around 5500 signatures. That’s not a bad reduction in signatures! Especially if your environment does not contain any systems such as those excluded.
Similarly, you can remove any Category that does not match your environment.
For example, if you do not have any Apache or Exchange Servers, you can safely exclude those categories too. So by doing some basic filtering you can safely turn down the amount of IPS work your firewall needs to do.
Customizing Sophos XG IPS Policies
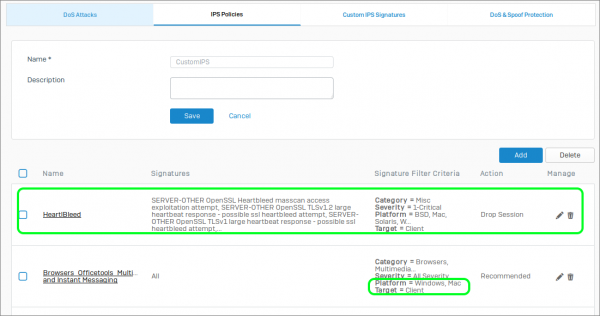
It is possible to customize the Sophos Intrusion Prevention System policies and rules to suit your needs. For example, let’s create our own IPS rule, and combine it with the recommended rules that apply to our specific environment.
The subject of this example is going to be the heart-bleed exploit.
- Navigate to Protect | Intrusion prevention | IPS Policies
- Click Add
- Give the Policy a new name such as "Custom IPS"
- For Clone Rules select LAN TO WAN
- Click Save
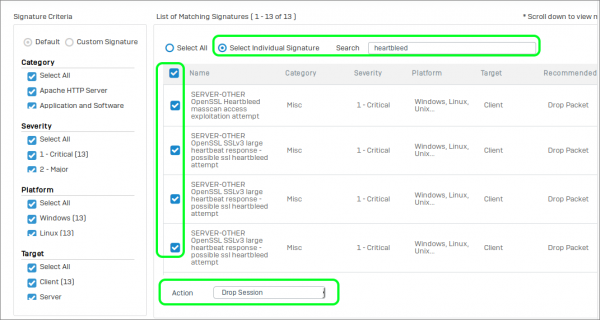
To enforce mandatory session dropping for heart bleed, we are going to add an additional rule to our IPS policy:
- Select your Custom IPS Policy
- Click Add
- Rule name: Heartbleed
- Select Select Individual Signature
- Seach for heartbleed
- Check the box next to the Name column heading to select all 13 instances
- Change the Action to Drop Session
- Click Save
You can now go through the rest of the rules based on Categories and filter out the Platform and Targets. You should now have a Custom IPS policy that looks as follows:
Conclusion
Enabling the comprehensive Sophos Intrusion Prevention System (IPS) protection on your Sophos XG is very easy.
For the most part, the Sophos Intrusion Prevention System is largely set and forget. It is continually tweaked for you by Snort and Sophos.
If you start to feel a performance hit, you can tune the default settings to match your actual environment.
The ability to have different IPS policies per firewall rules means you can have a very light "LAN TO LAN" IPS policy, but a far more comprehensive "LAN TO WAN" policy.
Take Fastvue Reporter for a test drive
Download our FREE 30-day trial, or schedule a demo and we'll show you how it works.
- Share this storyfacebooktwitterlinkedIn
How to Enable Dark Mode in Fortinet FortiGate (FortiOS 7.0)
Sophos XG - How to Block Searches and URLs with Specific Keywords